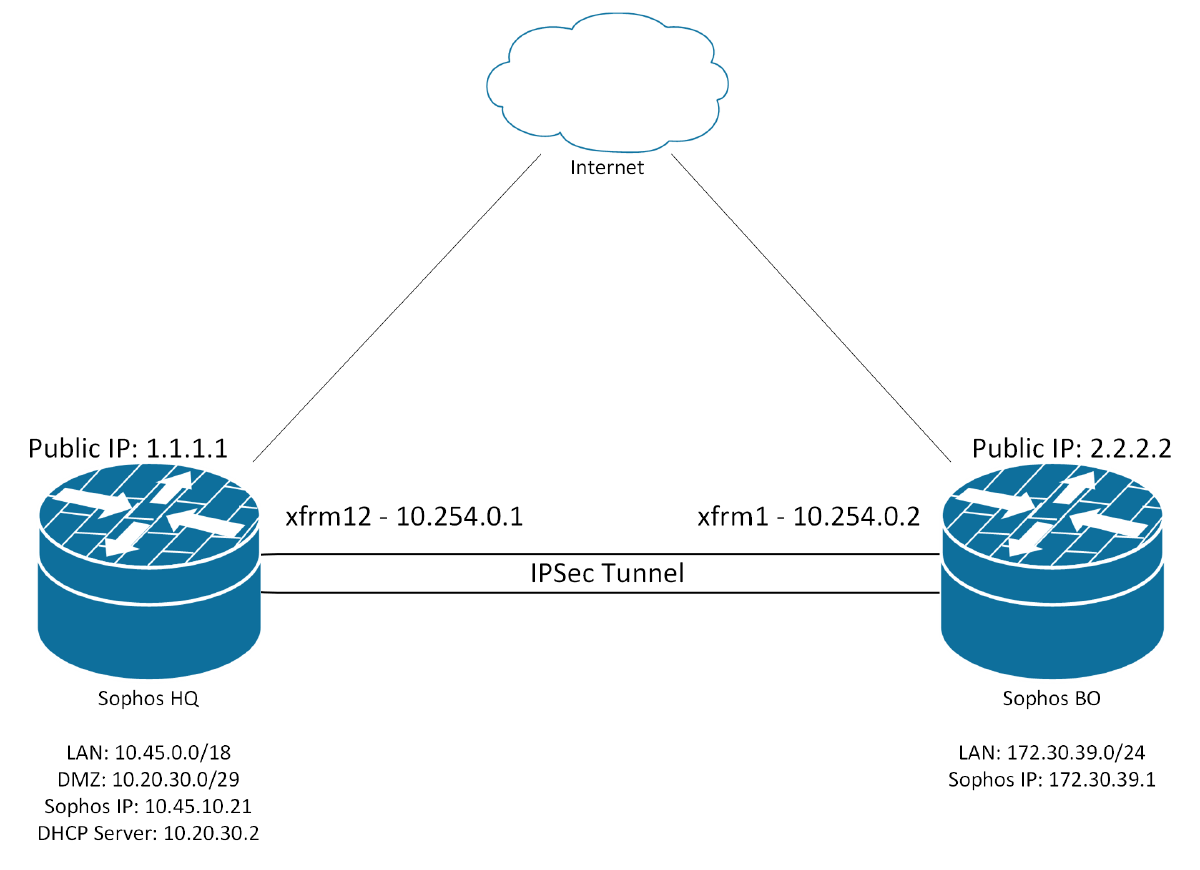
Configure the Sophos Firewall to function as a DHCP relay agent, enabling it to forward DHCP Discover and Request packets from local clients to a centralized DHCP server located behind the head office firewall. Ensure that the relay traffic is routed over an established route-based IPsec VPN tunnel for secure transmission.
Headquaters
DHCP
- Create a DHCP Scope in the DHCP Server 10.20.30.2
DHCP Range 172.30.39.200-254 Subnet mask 255.255.255.0 Default Gateway 172.30.39.1 DNS Servers 10.20.30.2, 172.30.39.1
IPSec
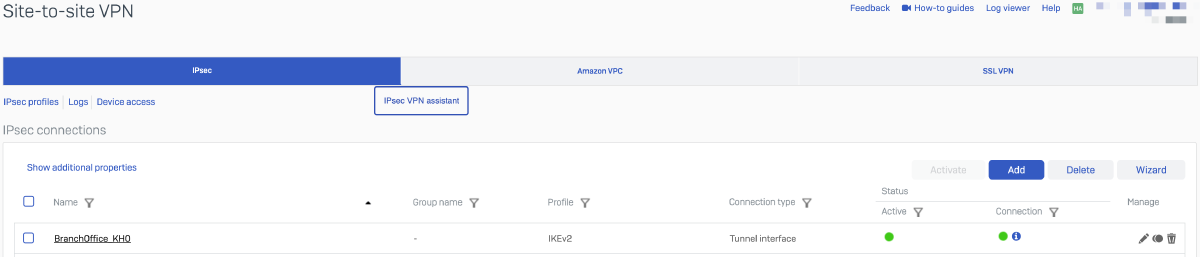
- Create an IPSec tunnel with VTI interfaces
Name Headquaters IP Version IPv4 Connection Type Tunnel interface Gateway type Responder Profile IKEv2 Authentication Type RSA Key — — Listening interface Port2 - 1.1.1.1 Local ID Type IP adddress Local ID 1.1.1.1 Local Subnet Any — — Remote Gateway address 2.2.2.2 Remote ID Type IP adddress Remote ID 2.2.2.2 Remote Subnet Any
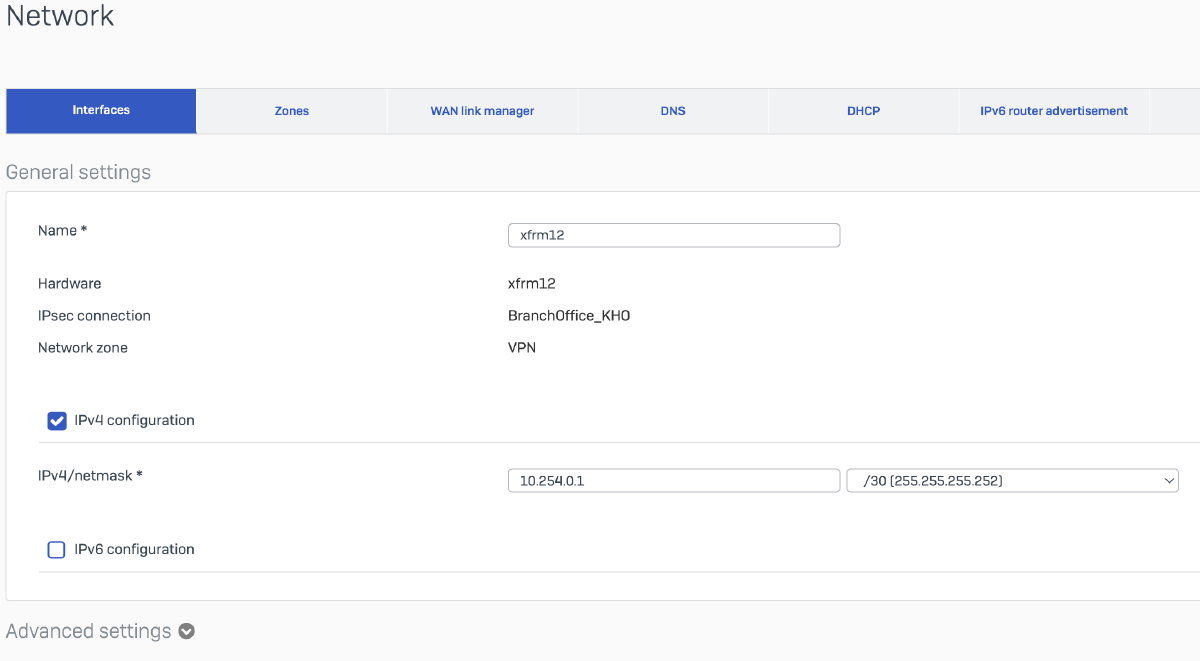
XFRM Interface
| IPv4 | 10.254.0.1 |
Route Traffic over IPsec
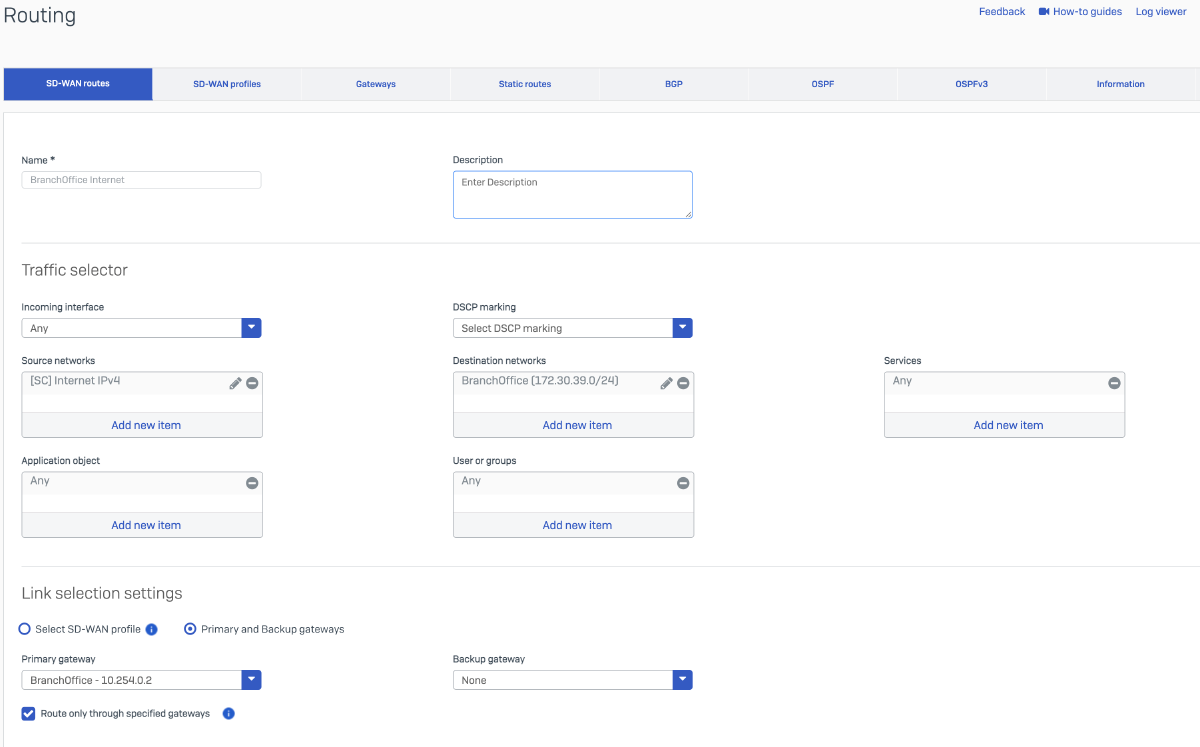
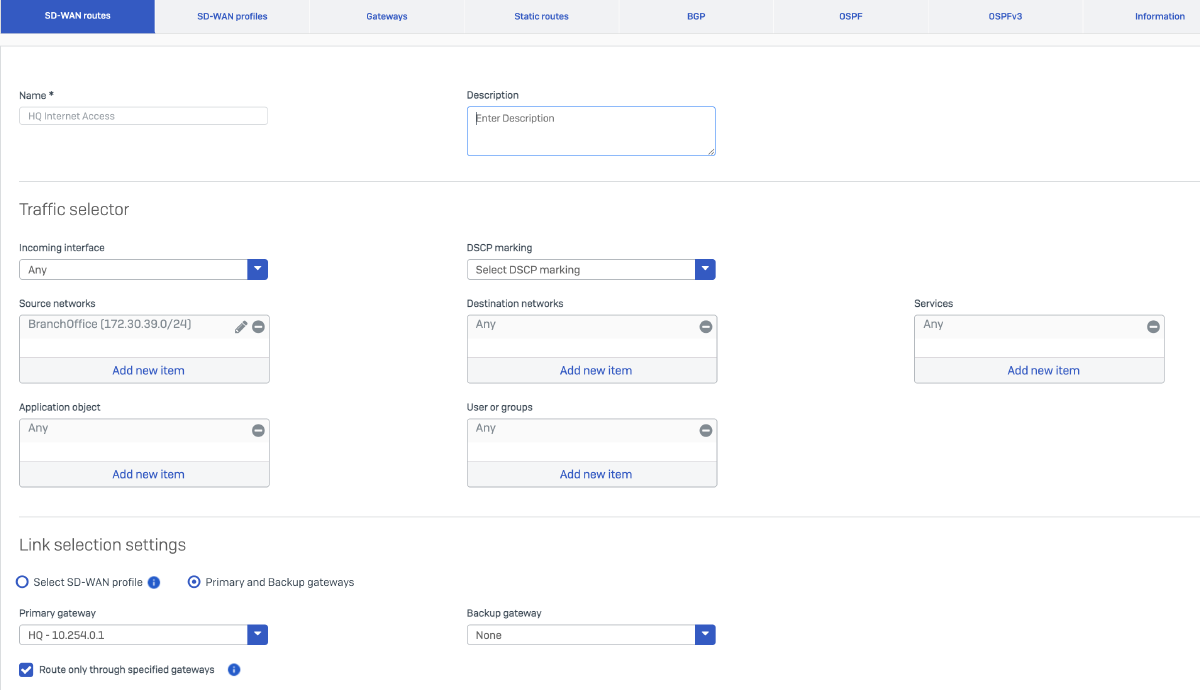
I will configure two SD-WAN routes on the HQ firewall. The first route will direct traffic from the internal DHCP server to the Branch Office firewall. The second route (optional) will route internet-bound traffic destined for the Branch Office network. This setup is intended to enable centralized internet breakout, allowing Branch Office traffic to be backhauled through the HQ firewall for internet access.
| Name | BranchOffice DHCP |
| — | — |
| Source Networks | DHCP Server (10.20.30.2) |
| Destination Networks | BranchOffice_Relay (172.30.39.1) |
| Services | DHCP |
| — | — |
| Link selection settings | Primary and Backup gateways |
| Primary gateway | BranchOffice - 10.254.0.2 |
| Route only through specified gateways | Checked |
| Name | BranchOffice Internet |
| — | — |
| Source Networks | Internet IPv4 (This is a hostgroup in Sophos Firewall) |
| Destination Networks | BranchOffice (172.30.39.0/24) |
| Services | Any |
| — | — |
| Link selection settings | Primary and Backup gateways |
| Primary gateway | BranchOffice - 10.254.0.2 |
| Route only through specified gateways | Checked |
HQ Firewall Rules
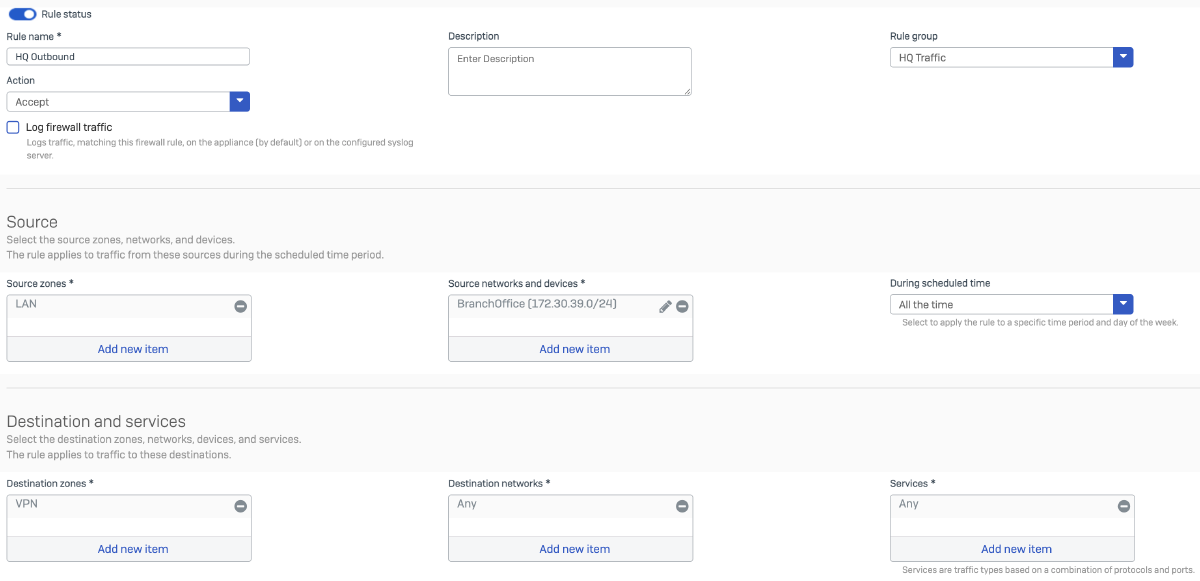
We will configure four firewall rules on the HQ firewall:
Rule 1: Permits DHCP relay traffic from the Branch Office firewall to the DHCP server located in the HQ network, allowing DHCP Discover and Request messages to be forwarded appropriately.
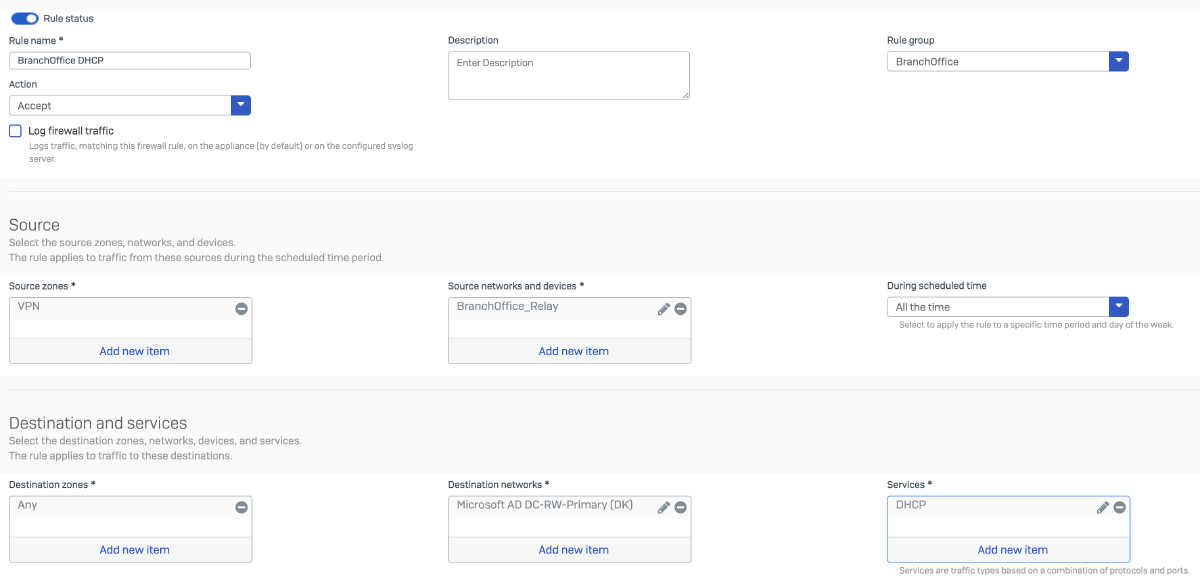
Rule 2: Allows Branch Office network to make DNS queries on the DHCP Server.
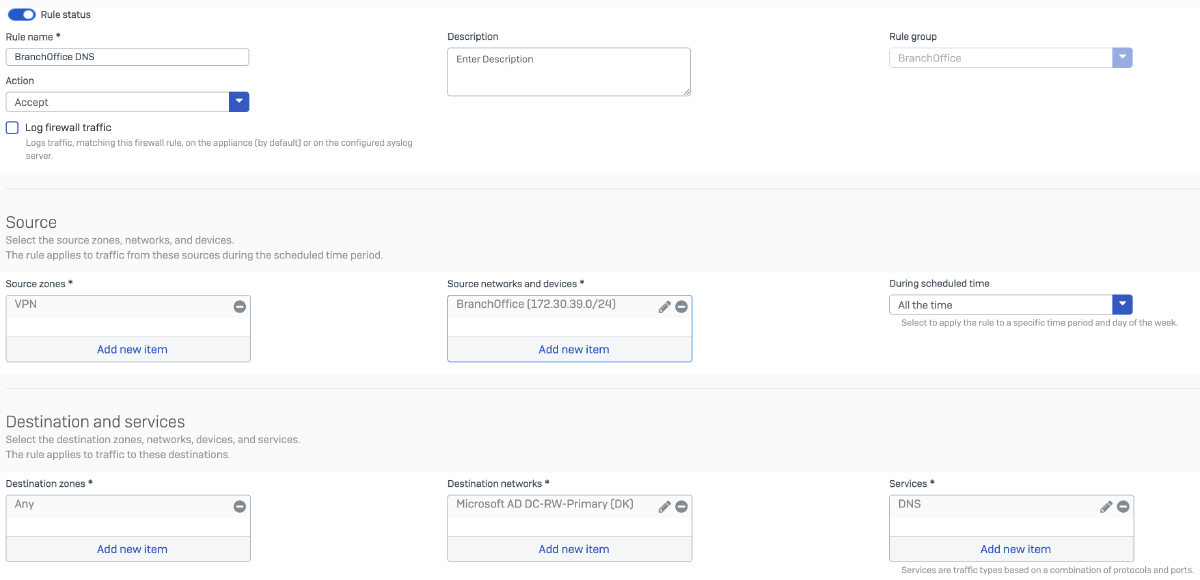
Rule 3: Allows internet-bound traffic originating from the Branch Office network to traverse the HQ firewall for centralized internet access.
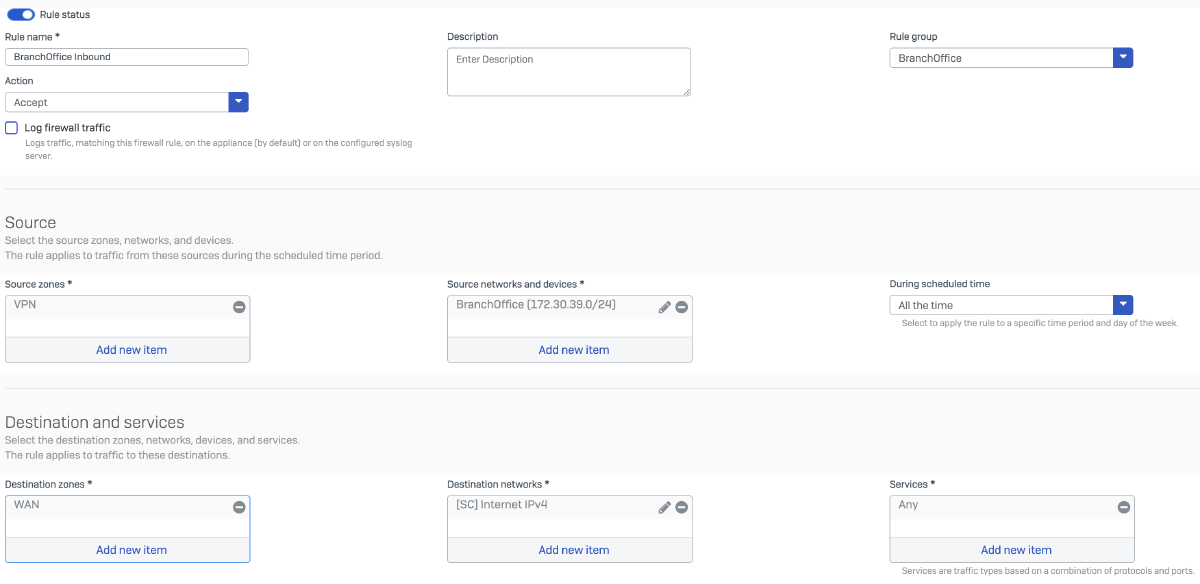
Rule 4: Enables return traffic from the internet to reach the Branch Office network, completing the flow for NAT and stateful inspection.
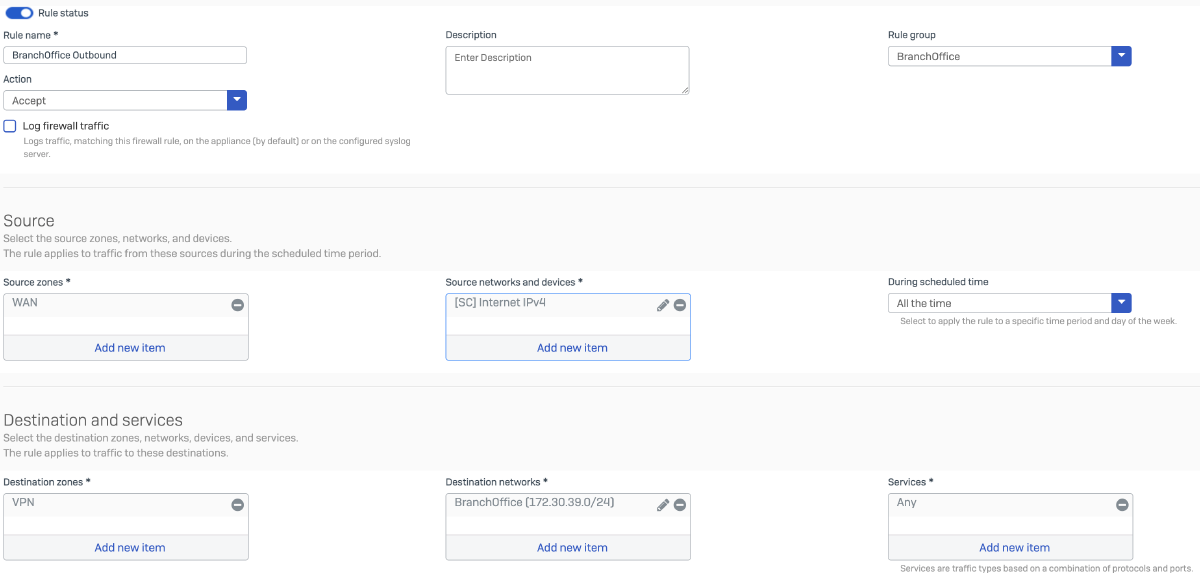
Branch Office
IPSec Branch Office
| Name | Branch Office |
| IP Version | IPv4 |
| Connection Type | Tunnel interface |
| Gateway type | Initiate the connection |
| Profile | IKEv2 |
| Authentication Type | RSA Key |
| — | — |
| Listening interface | Port2 - 2.2.2.2 |
| Local ID Type | IP adddress |
| Local ID | 2.2.2.2 |
| Local Subnet | Any |
| — | — |
| Remote Gateway address | 1.1.1.1 |
| Remote ID Type | IP adddress |
| Remote ID | 1.1.1.1 |
| Remote Subnet | Any |
XFRM Interface
| IPv4 | 10.254.0.2 |
Branch Office DHCP
Configure a DHCP relay on the Branch Office router. Specify the LAN interface (BranchOffice - 172.30.39.1) as the source interface for relay operations. Set the DHCP server IP address to 10.20.30.2. Ensure the option ‘Relay through IPsec’ is enabled to forward DHCP packets securely over the IPsec tunnel.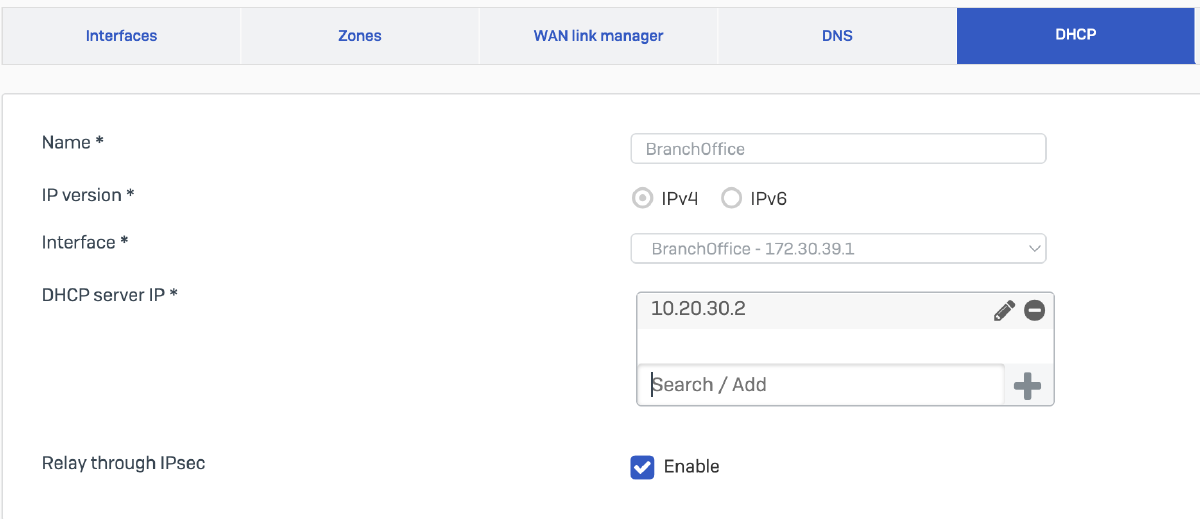
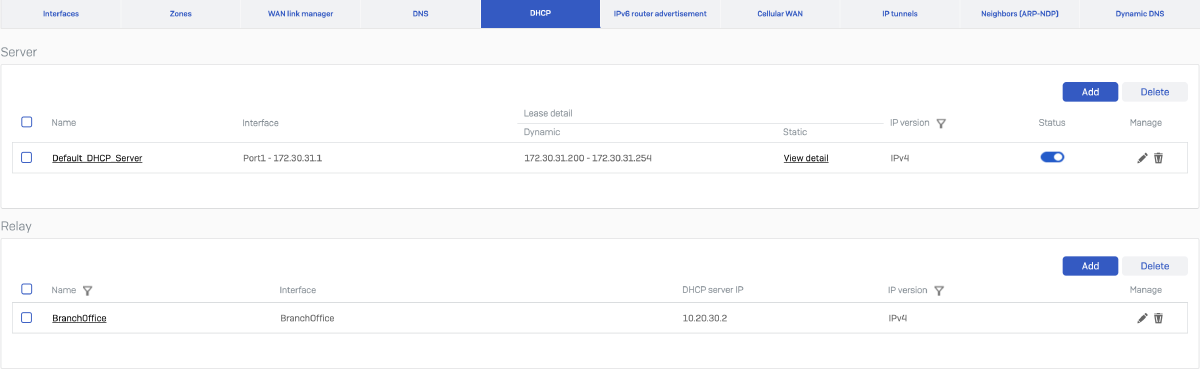
Configure IPsec Route and Source NAT for System-Generated Traffic to DHCP Server
On the Branch Office firewall, configure an IPsec route to ensure system-generated traffic (e.g., DHCP relay packets) is forwarded to the DHCP server located at the Head Office via the IPsec tunnel. Additionally, apply source NAT to translate the internal source IP (originating from the Branch Office LAN interface) to the DHCP server’s IP at the Head Office to ensure proper routing and response.
Access the Device Console:
From the CLI menu, select option 4 for the Device Console.Configure System Traffic Source NAT:
Apply source NAT to translate the firewall’s LAN interface IP (used by the DHCP relay agent) to the destination DHCP server IP. This ensures the return traffic is correctly routed.set advanced-firewall sys-traffic-nat add destination <DHCP_Server_IP> snatip <Branch_LAN_Interface_IP> Example: set advanced-firewall sys-traffic-nat add destination 10.20.30.2 snatip 172.30.39.1
Note: These commands are essential for relayed DHCP packets initiated by the firewall to be transmitted over the IPsec tunnel and correctly processed by the remote DHCP server.
Branch Office SD-WAN Route
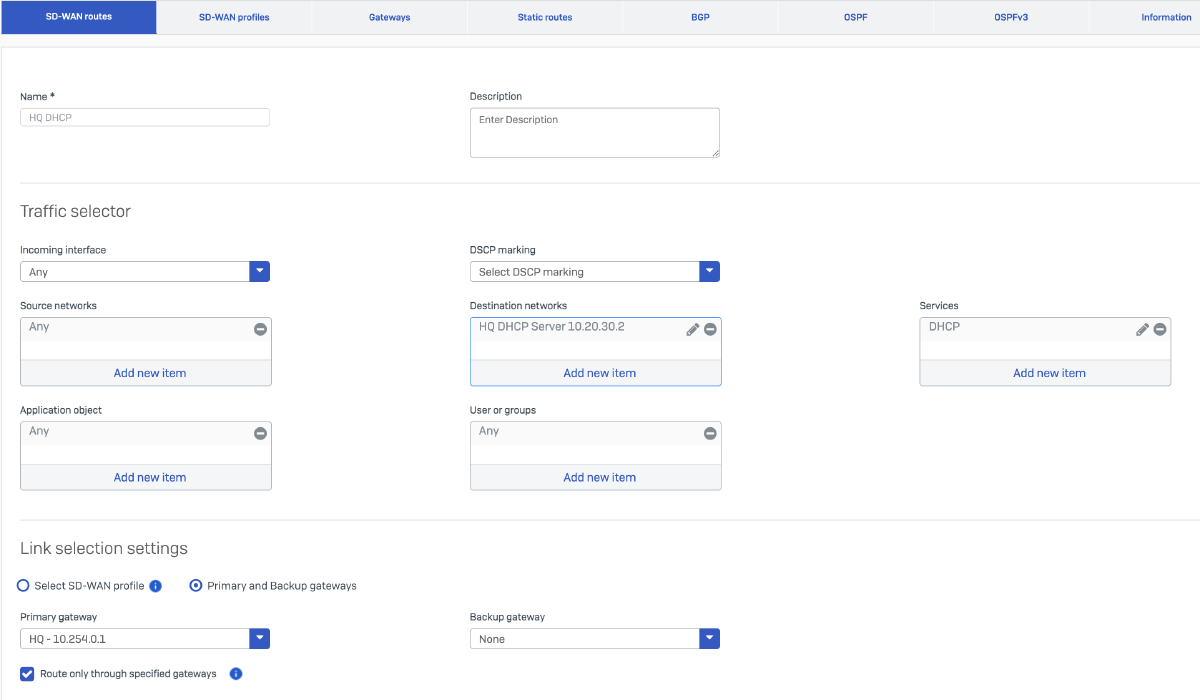
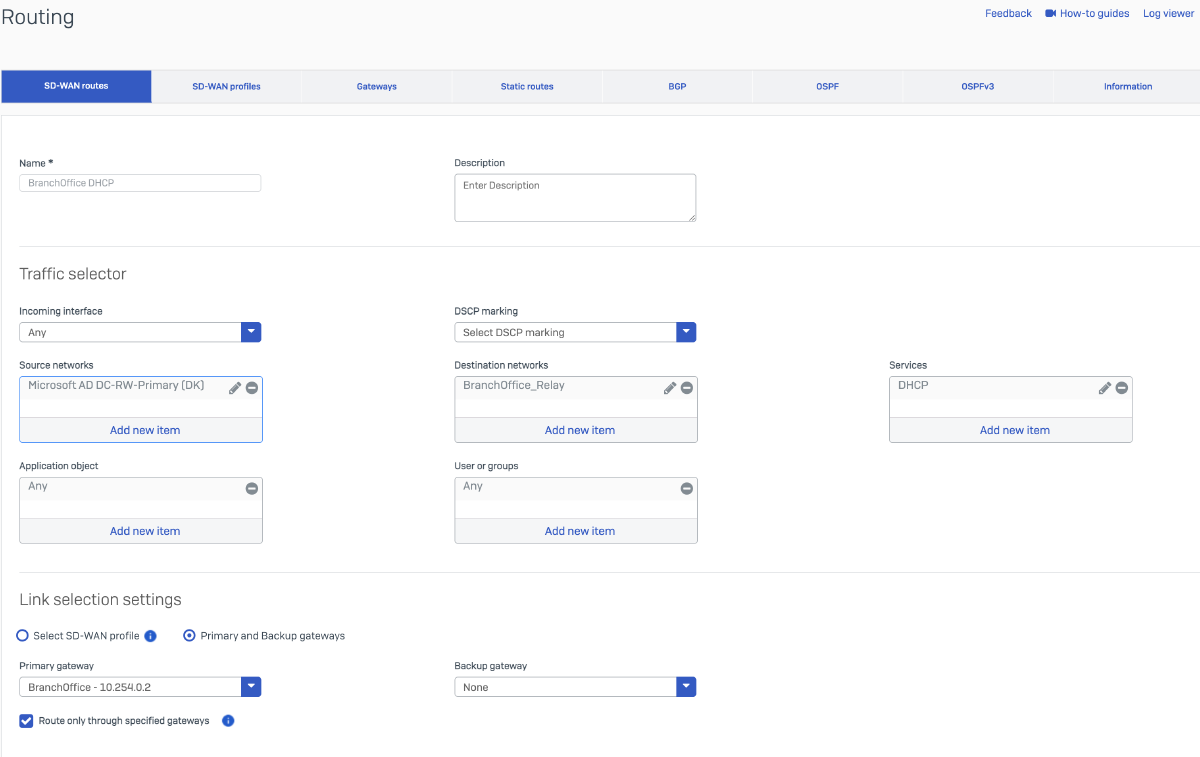
I will configure two SD-WAN routes on the Branch Office firewall. The first route will forward DHCP relay traffic from the Branch Office to the DHCP server located at the Head Office. The second route (optional) will direct internet-bound traffic from the Branch Office network through the IPsec tunnel to the Head Office, enabling centralized internet breakout. This setup ensures that all Branch Office internet traffic is backhauled via the HQ firewall for unified security and policy enforcement.
| Name | HQ DHCP |
| — | — |
| Source Networks | Any |
| Destination Networks | HQ DHCP Server (10.20.30.2) |
| Services | DHCP |
| — | — |
| Link selection settings | Primary and Backup gateways |
| Primary gateway | HQ - 10.254.0.1 |
| Route only through specified gateways | Checked |
| Name | HQ Internet |
| — | — |
| Source Networks | BranchOffice (172.30.39.0/24) |
| Destination Networks | Any |
| Services | Any |
| — | — |
| Link selection settings | Primary and Backup gateways |
| Primary gateway | HQ - 10.254.0.1 |
| Route only through specified gateways | Checked |
Branch Office Firewall Rules
Inbound Access to Branch Office Network:
Create a firewall rule to allow inbound traffic destined for the Branch Office LAN subnet 172.30.39.0/24. This rule should permit traffic arriving over the IPsec tunnel or other trusted interfaces, based on your topology and security policies.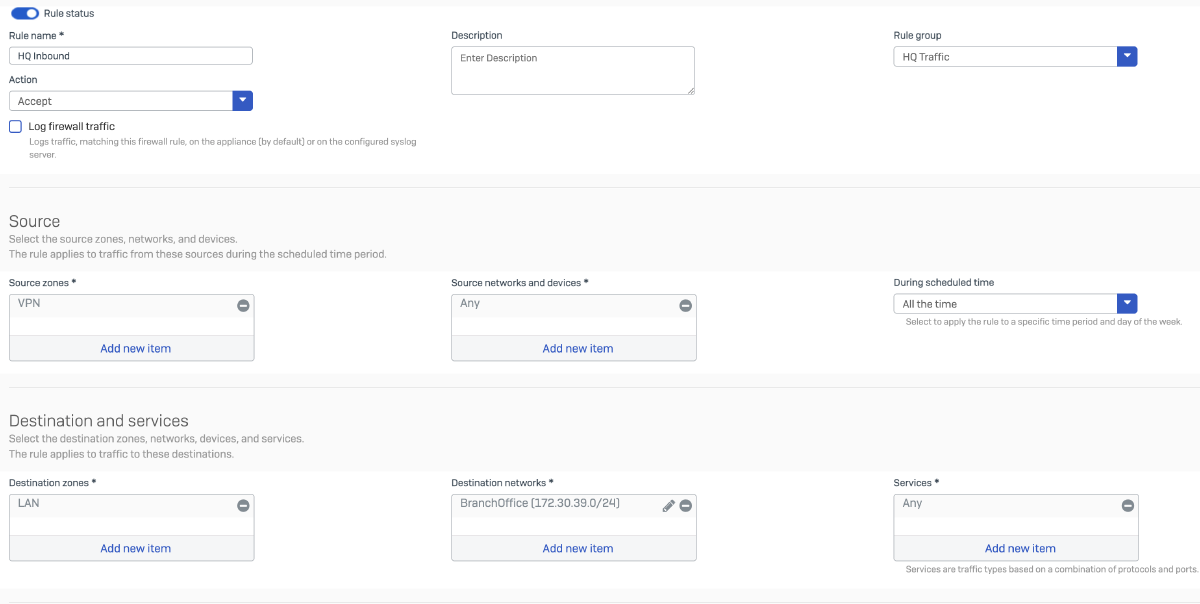
Outbound Access from Branch Office to HQ:
Define a firewall rule to allow outbound traffic originating from the Branch Office subnet 172.30.39.0/24 towards the Head Office network. This rule enables inter-site communication over the IPsec VPN tunnel and ensures proper routing of internal services such as DHCP, DNS, or centralized internet breakout.